As ecommerce and the number of digital transactions keep growing, cybercriminals are using increasingly advanced methods to scam companies and consumers. Among the most severe cyber threats are the so-called Magecart attacks that have been causing havoc in all kinds of online industries.
But what exactly is Magecart? And what are Magecart attacks? And, even more importantly, how can you protect your business from them? Keep reading to learn all about one of the the biggest threats to your ecommerce site – and how you can mitigate the risks.
What are Magecart Attacks?
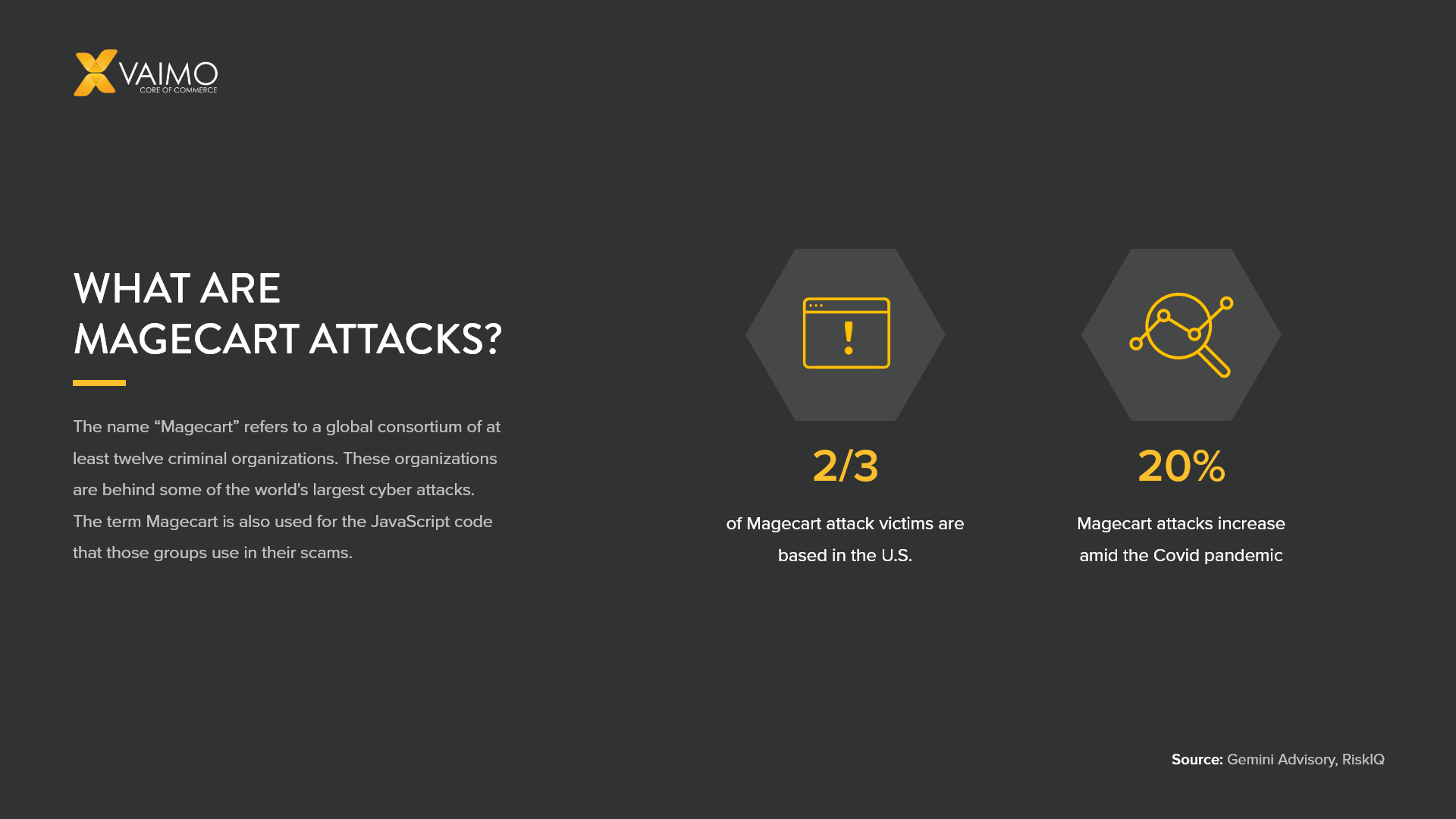
Let’s start from the beginning. The name “Magecart” refers to a global consortium of at least twelve criminal organizations. These organizations are behind some of the world’s largest cyber attacks. Also sometimes referred to as front-end attacks, their modus operandi is better known as Magecart attacks. The term Magecart is also used for the JavaScript code that those groups use in their scams.
Typical for these attacks is that they use the client-side browser to access information entered by online customers. The attacks target and collect sensitive customer data (email addresses, passwords, and credit card numbers) by injecting malicious JavaScript code.
Unfortunately, the Magecart methods are very advanced and constantly evolving. One classic example of a Magecart attack involves injecting brand new fields into online forms to collect sensitive information. Customers have no way of knowing that they’re visiting a compromised page, and businesses usually only find out about the scam long after the damage has already occurred.
Other times, Magecart attacks target a company’s 3rd party providers. Today, it’s common for ecommerce merchants to use third-party scripts on their sites to provide good customer experiences.
These solutions have many benefits and generally make it easier, cheaper, and faster to develop and add new functionality to websites. However, they also introduce an element of risk, as using third-party scripts means that website owners are not in complete control of the entire code. An ecommerce website today may have code from tens of different third parties that all have the same privileges as the main code, and scammers know how to take advantage of this.
How Common are Magecart Attacks?
As this is a very lucrative crime, the number of Magecart attacks is only growing–with devastating effects for businesses and customers alike. Magecart skimmers have attacked more than 2 million global websites, and the number of incidents increased by more than 20% during the pandemic.
Add to this the fact that online shopping is at its highest level ever in the wake of COVID-19, and you have the perfect breeding ground for Magecart attacks.
Real-world Examples of Magecart Attacks
When it comes to Magecart attacks, everyone is at risk. No industries are spared, and the Magecart victim list reads like a who’s who of some of the world’s leading brands. Magecart attacks target all kinds of businesses of all sizes and segments, and with increasingly complex methods.
Let’s have a look at some high profile examples:
- One of the giant spikes in Magecart attacks came in 2018 when Ticketmaster announced that payment information had been stolen from their websites. Research from RiskIQ showed that the breach resulted from Magecart operatives placing skimmers on checkout pages through third-party suppliers. They also attacked third parties themselves, which gave the scammers access to over 800 ecommerce sites.
- Websites of 8 US cities were compromised by Magecart card detail-skimming software. The skimmers targeted payments made through Click2Gov (a self-service portal used to pay utility bills and parking fees). In this case, attackers were collecting credit card details along with names and contact addresses.
- In February 2020, RiskIQ found that Magecart Group 8 had placed a JavaScript skimmer on NutriBullet’s international website to steal credit card information. Despite efforts to remove the skimming code, new versions kept appearing, compromising the site for almost a whole month.
- Airline giant British Airways was targeted by a Magecart attack in 2018, and the data of nearly 400,000 customers was breached. The Magecart attack affected payments on the main site and mobile app between August 21st, 2018, and September 5th, 2018. As a result, British Airways had to pay a record-high £183m GDPR fine after failing to prevent the attack.
- Magecart has also targeted the magazine industry with an attack on Forbes. This time, attackers injected web-skimming scripts into the subscription website for the Forbes print magazine. Customers thought they were signing up to get Forbes delivered to their door but were instead delivering their sensitive information straight into the hands of hackers.
This is just a handful of examples that illustrate the extent and potential devastation of a Magecart attack. And with the increase in online shopping, they’re showing no signs of slowing down.
Related reading: COVID-19 pandemic is fuelling a surge in cyber attacks
5 Different Types of Magecart Attacks
Magecart hackers operate in many different ways, and unfortunately, they keep adding new methods to their repertoire. Below, we’ll have a closer look at five of the most common types of attacks:
“Ant & Cockroach” Skimming
This is one of the most prevalent types of Magecart attacks. It usually targets URLs linked to a website’s checkout page and uses the “Radix” obfuscation technique to hide the malicious code. The name comes from the fact that the words “ant” and “cockroach” were sprinkled throughout the malicious skimming code used in the first attacks of this kind.
Compromising the Supply-chain
Supply chain compromises are a typical Magecart trait. This kind of attack is usually done by injecting skimming code as third-party code on websites. Often, the hackers will use credential theft, RDP attacks, or SQL injection to gain access to the third-party’s servers and insert the malicious code. This code is designed in a way that evades detection, allowing the hacker to steal customer data from website visitors.
Skimming Through CDN and IFrames
Magecart skimmers often take advantage of content delivery networks and the associated JavaScript files to hide their payload. For example, the hackers may use a domain that closely resembles a legitimate product, then redirect visitors to it, and implement their malicious JavaScript there.
This way, the attackers can collect customer data like credit card information at the checkout. Skimmers have also been known to inject fake PayPal iframes on vulnerable websites, hijacking and compromising the payment process to steal sensitive credit card information. A report from RiskIQ in 2020 identified a new Magecart group that they named ‘MakeFrame’ based on its ability to make iframes for skimming payment data.
Hiding Skimming Scripts in Image Files and Favicons
This type of skimming attack is relatively new and was first detected on the WooCommerce WordPress plug-in in 2020. Hackers would use the metadata of image files to hide their malware and steal the credit card information entered by online customers. The metadata of an image file contains several fields of information, such as date, time, resolution, and the hackers would, for example, use the copyright field to hide their code.
Another way of hiding the malware is to insert it into websites through PHP-based shells disguised as favicons. Hackers do this by replacing the shortcut tags in the code to reference the malicious image file instead. This shell can then skim credit card information from domains.
Attacking Outdated Ecommerce Software
In 2020, over 2,800 websites running Magento’s old-version software were attacked by skimmers. These attacks are known as Cardbleed, and together, they were one of the biggest attacks ever carried out by the Magecart group. The hackers connected with (the outdated version of) the Magento admin panel and executed malware. That malware was then deleted, but only after having compromised an important JavaScript file.
Hacker Attacks Cause Serious Damage
Being subjected to a Magecart attack can have devastating consequences both for brands and for their customers. Data breaches undermine trust, can lead to substantial losses, and also result in huge fines. Let’s have a closer look at some of the different ways cyber-attacks can harm businesses:
- Damage to your brand: When people learn that credit card information and personal details have been compromised via your brand, they become hesitant to use your site. And as we saw in the NutriBullet example, one skimming attack followed after another, so it’s not irrational for customers to be on the fence. The often recurring nature of Magecart attacks will have customers leaving your site as soon as your brand is mentioned in the same sentence as ‘Magecart.’
- Operational disruption: A data breach will affect your daily operations until a solution is found, which can lead to delayed deliveries, payments, and a damaged customer experience.
- Financial loss: Losing customer trust will inevitably impact your bottom line. Whether it’s due to decreased footfall on your site or because you’re unable to transact while an incident is investigated, Magecart attacks can cause severe financial damage to your business.
- Regulatory issues and fines: it’s not just loss of customers and sales that can cost you dearly as the result of an attack. As we saw in the case of British Airways, the regulatory and legal ramifications of data breaches can entail enormous fines.
Processes are Key in Ecommerce Security
The first line of defense against Magecart (or any other cyber-attack) is your people, your organization, and your processes. In our earlier article, we walked through some of the steps your business needs to take to keep security top of mind to mitigate the risks. Human error causes a majority of security breaches, which, on the bright side, means they’re preventable.
Here are some of the ways you can strengthen your protection to prevent attacks:
- Foster a culture of cybersecurity. Encourage and incentivize employees to follow good security practices from their first day on the job.
- Develop security governance documentation. Clear and thorough documentation is vital and should include both security policies and a response plan should the worst happen.
- Invest in continuous employee training. Education is key to making security an integral part of your culture. The best way to get people to follow policies and practices is to help them understand why they are so important and what the risks are.
- Make sure that your software, hardware, and tools are up to date. Older devices and software that are outdated are more vulnerable to attacks. And if your employees use their own devices at work, then make sure that these are held to the same standards and that they follow the same security policies.
- Test your staff and processes. Just like we need fire drills to be prepared for physical emergencies, we also need to test different emergency scenarios in the digital environment. The goal should be to identify weaknesses in your security system and not to single out individual employees if they make mistakes.
Human error is just that, very human, and the only remedy is constant training and vigilance. Mistakes are often made with good intentions and caused by a lack of education, time pressure, insufficient internal processes, and day-to-day distractions. Most of us have been in situations where someone shares their username with a colleague to speed things up, and unfortunately, it doesn’t take more than that to potentially cause a disaster.
Related reading: Cybersecurity Education for Your Business
Get the Tools to Protect Your Business
Following the above steps are crucial in keeping you and your customers safe. But as we’ve seen, Magecart attacks present a new and complex set of challenges.
They are virtually impossible to detect with the naked eye, and it often takes companies months to discover they’ve been hacked, by which time their site is already compromised. And even when removed, malware might not be eliminated, meaning it can get back into your online store, as illustrated by the case of NutriBullet. To have a chance of discovering malicious software, constant monitoring of your website is a must.
A Multi-layered Approach to Ecommerce Security
Adopting a multi-layered approach to security will give your business the best possible protection and prevent attackers from penetrating your site and systems. Some of the tools needed to do this include:
- Weak password detection
- Web application firewall
- Intrusion detection system
- Log manager system
- Content Delivery Network (CDN) to protect against distributed denial-of-service attacks
- Vulnerability scanning assessment
- Security dashboards
- Data breach monitoring (Data loss prevention tools)
Each tool in this toolbox is important, as a chain is never stronger than its weakest link. Partnering with experienced experts in digital security is usually the best way to ensure all i’s are dotted and all t’s are crossed.
Magecart attacks keep getting more and more sophisticated and challenging to discover. The happy news is that there are ways to detect attacks and protect your business against attacks. At Vaimo, we’re experts in all things ecommerce and would love to support you in building a solid strategy for your digital security.
Data Breach Monitoring and Instant Alerts
To prevent Magecart attacks, you will need to leverage advanced digital security technologies. Our Data Breach Monitoring Service is one way for you to leverage world-class security technology to protect your site against attacks.
This tool immediately detects if your site is compromised and alerts the Vaimo team and yourself. It does this by running scripted user journey tests regularly during the day, comparing the outgoing server addresses to the addresses whitelisted on your site.
Security Audits
We offer security audits where we perform automated checks and manual assessments of your web application and infrastructure. This way, we can identify vulnerabilities in your system and provide you with suitable recommendations for improving your digital security. The security audit includes:
- Manual assessment
- Infrastructure security testing
- Vulnerability assessment
Penetration Testing
We also offer a penetration testing service to help you understand where your system is most exposed to risk. Our penetration tests mimic actual hackers’ activities and show you where there may be weaknesses leaving your business vulnerable to attack. We go beyond preventing criminals from accessing your systems and create real-world scenarios to show you exactly how your current system would respond in the case of a cyber-attack.
How Vaimo Can Help
With the services we provide, we reduce the possible impact caused by data breaches to minutes instead of days, weeks, or even months. You can read more about our data breach monitoring tool here or watch this webinar to learn more about how we work with security.
Get in touch with our team today to learn more about how we can protect you and your business from Magecart attacks and other cyber threats.
 |
OLGA GUTENKOBUSINESS DEVELOPMENT MANAGER FOR SECURITYAny questions? Feel free to reach out to me directly! |